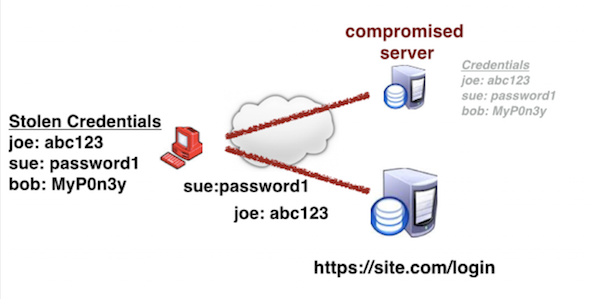
Credential Stuffing is the simplistic automated insertion of stolen usernames and passwords into web application login fields with the end goal of account takeover (ATO) and its attendant fraud. Credential stuffing relies on the shared secret model of user authentication, chiefly by enabling any person in the possession of static access credentials to present themselves as an authorized user.
In credential stuffing, hackers obtain user credentials from past data breaches by purchasing them at low cost on the dark web. They then develop rudimentary scripts to automatically “stuff” username and password combinations into the login fields of web applications until a fortuitous match is found. The credential stuffing success rate is estimated to be around 2-4 percent. When a match is found, the consequences can be ATO for consumer financial fraud or corporate account takeover (CATO) for more serious crimes by abusing victim access privileges.
Credential stuffing attacks are inexpensive to launch, expensive to defend against, and have high success rates. The automation tools to launch an attack are easy to develop or buy, even for a script kiddie. What drives credential stuffing perpetrators' actions is users’ persistent likelihood to reuse passwords across different online services in their personal and work lives.
Credential stuffing attacks often employ a bot or botnets to spray credentials and combinations thereof into the login fields of web apps until a match is made.
Example:
"Last year my payment provider fell victim to a large-scale credential stuffing attack. Apparently my password was one that I had reused from my Yahoo account, and was used by the attackers to compromise my account."
Hear From a CISO about Credential Stuffing: