An adversary-in-the-middle (AitM) attack, also known as a man-in-the-middle (MitM) attack, is a type of cyberattack where a perpetrator positions themself in a conversation between two parties — two users, two devices, or a user and an application or server — so that all communications are going to or through the attacker. Adversary-in-the-middle is the official term used in the MITRE ATT&CK® framework.
Contrary to a traditional phishing setup, AitM phishing does not require a custom built phishing site, but rather the requests are proxied to and from the actual website.
AitM Example:
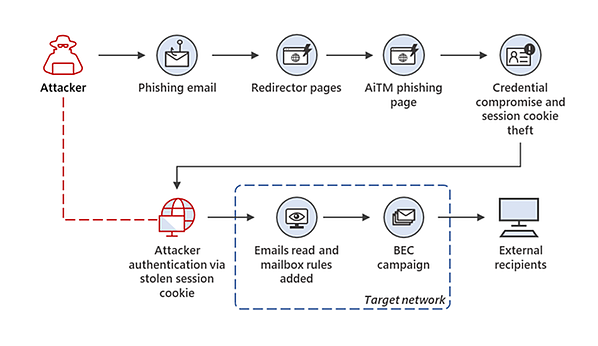
"In July 2022, Microsoft reported a new type of phishing attack that bypassed MFA controls using an adversary-in-the-middle attack to steal session cookies and gain access to victims' email accounts. Once they had gained access to mailboxes the attackers followed up with Business Email Compromise (BEC) attacks."
Illustration of an AitM Attack Flow:
Source: Microsoft